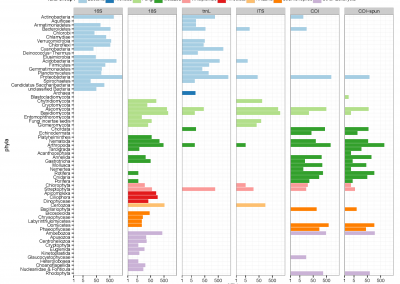
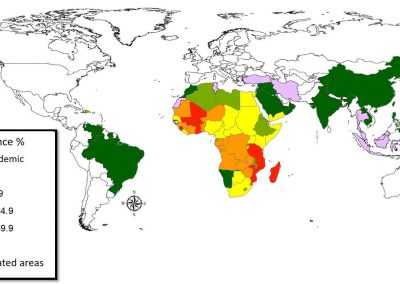
Mobile Click Fraud Attack (MCFA)
Elliott Wen, Doctoral Candidate; Dr Gerald Weber, Senior Lecturer, Department of Computer Science
A series threat: Mobile Click Fraud Attack
Nowadays, Mobile Click Fraud Attack (MCFA) is becoming a frequent topic within cyber security experts community. In an attack such as Click Fraud, malicious individuals repeatedly generate click events on mobile applications with the intention to increase revenues or exerting personal influence. Common examples include boosting product ratings or increasing the `like’ number in social media pages. Shockingly, such attacks are known to have caused a substantial damage of US$16.7 billion on mobile application economy in 2017.
In general, most of these attacks are carried out by automating a massive number of physical devices. But, to purchase a large volume of devices would have incurred substantial costs. Therefore, a cheaper alternative to the physical devices is to use emulators. However, current existing emulators are inefficient and vastly blocked due to their immense resource demand and defective device signatures. In this research, we propose a programme called Fraus – a cost efficient and scalable approach to conduct large-scale click fraud using device emulators.
Fraus maintains a low resource profile by circumventing graphics emulation and applying lazy-loading techniques on system components. In addition, Fraus provides a seemingly authentic device signature and disguises itself as a legitimate device by fully emulating the missing hardware components including WiFi interfaces and cellular modems. To facilitate the management of numerous emulator instances, Fraus also offers a distributed management system, which is scalable and fault-tolerant.
We evaluated the performance of Fraus by mocking attacks against the top 300 applications from the Google Play store. The results demonstrate that Fraus has high system stability and application compatibility.
Fraus also significantly reduces CPU usage and memory footprint by 90% and 60% respectively when compare it with the existing emulators.
By designing Fraus, we aim to raise public concerns about the simplicity of committing click fraud and to suggest countermeasures to mitigate such risks.
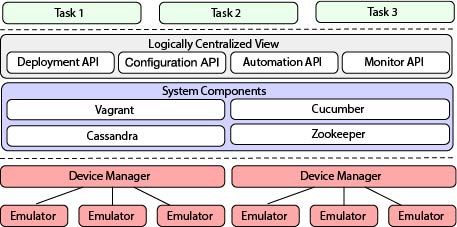
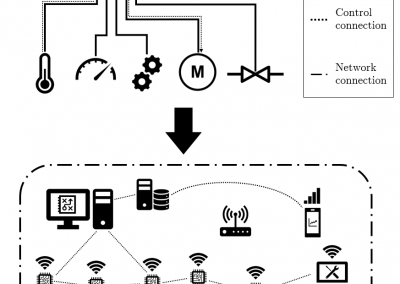
Figure 1. System Architecture of Fraus
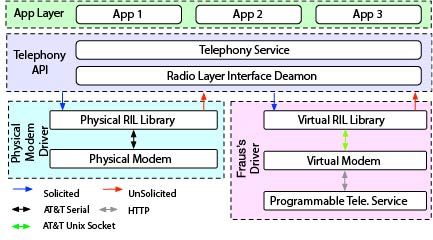
Figure 2. Overview of Android Telephony Architecture
Support from the Centre for eResearch
This research involves extensive compiling tasks of the Android source codes. The whole process may take up to 3 hours in a normal desktop machine. The long-lasting waiting greatly impact the research progress.
Thanks to the staff at CeR who assisted our group gaining the access to the virtual machines with abundant CPU cores and terabytes of high-speed data storage, which significantly boost our research progress. Meanwhile, CeR created ready-to-go compiling environment for us, which is quite helpful as our research group can simply focus on our research targets without tuning the complicated settings of the virtual machines.
See more case study projects

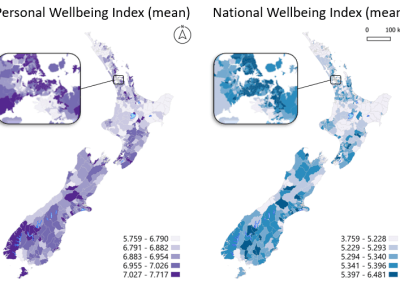
Our Voices: using innovative techniques to collect, analyse and amplify the lived experiences of young people in Aotearoa
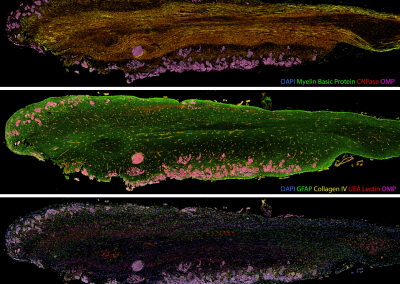
Painting the brain: multiplexed tissue labelling of human brain tissue to facilitate discoveries in neuroanatomy

Detecting anomalous matches in professional sports: a novel approach using advanced anomaly detection techniques

Benefits of linking routine medical records to the GUiNZ longitudinal birth cohort: Childhood injury predictors

Using a virtual machine-based machine learning algorithm to obtain comprehensive behavioural information in an in vivo Alzheimer’s disease model
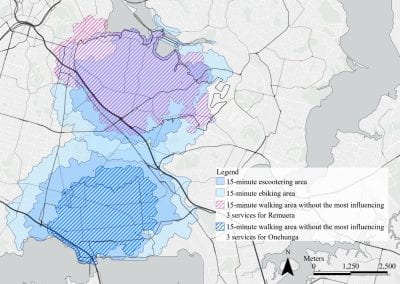
Mapping livability: the “15-minute city” concept for car-dependent districts in Auckland, New Zealand

Travelling Heads – Measuring Reproducibility and Repeatability of Magnetic Resonance Imaging in Dementia
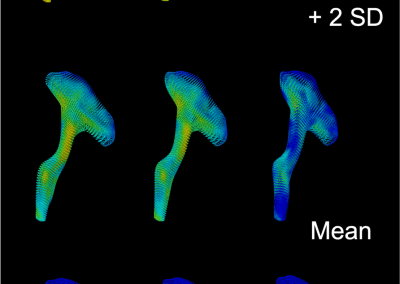
Novel Subject-Specific Method of Visualising Group Differences from Multiple DTI Metrics without Averaging

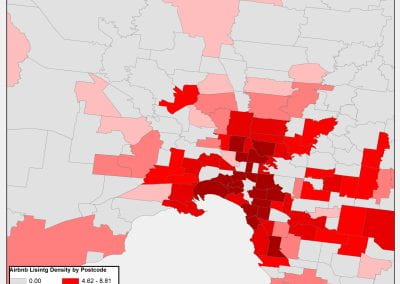
Re-assess urban spaces under COVID-19 impact: sensing Auckland social ‘hotspots’ with mobile location data
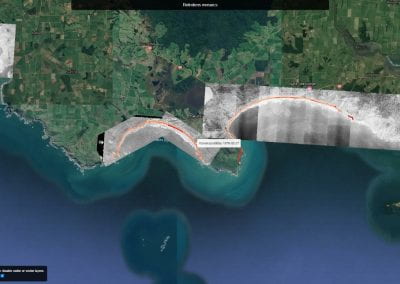
Aotearoa New Zealand’s changing coastline – Resilience to Nature’s Challenges (National Science Challenge)

Proteins under a computational microscope: designing in-silico strategies to understand and develop molecular functionalities in Life Sciences and Engineering
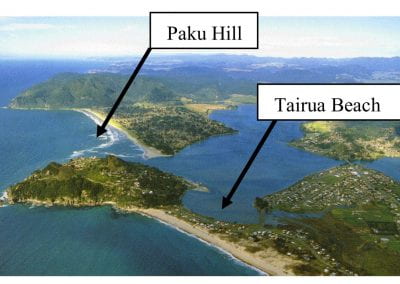
Coastal image classification and nalysis based on convolutional neural betworks and pattern recognition
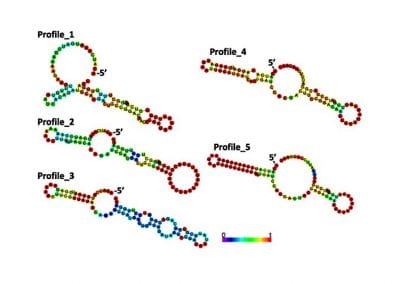
Determinants of translation efficiency in the evolutionarily-divergent protist Trichomonas vaginalis
Measuring impact of entrepreneurship activities on students’ mindset, capabilities and entrepreneurial intentions

Using Zebra Finch data and deep learning classification to identify individual bird calls from audio recordings

Automated measurement of intracranial cerebrospinal fluid volume and outcome after endovascular thrombectomy for ischemic stroke

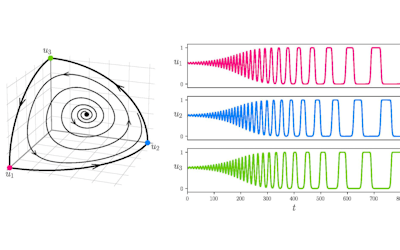
Using simple models to explore complex dynamics: A case study of macomona liliana (wedge-shell) and nutrient variations
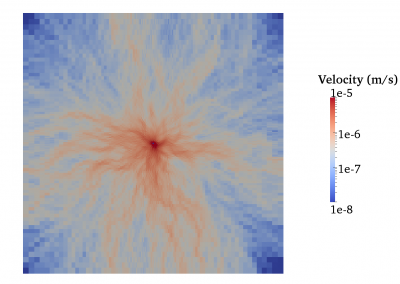
Fully coupled thermo-hydro-mechanical modelling of permeability enhancement by the finite element method

Modelling dual reflux pressure swing adsorption (DR-PSA) units for gas separation in natural gas processing
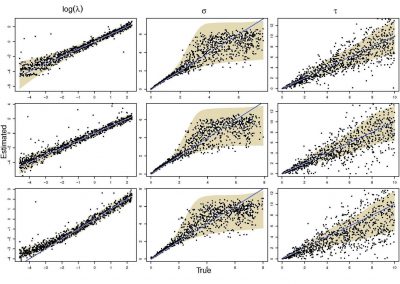
Molecular phylogenetics uses genetic data to reconstruct the evolutionary history of individuals, populations or species
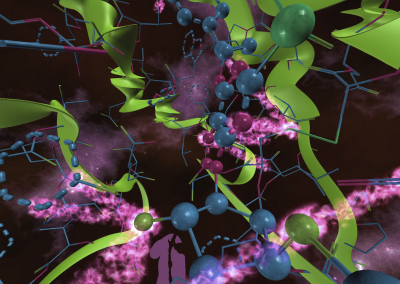
Wandering around the molecular landscape: embracing virtual reality as a research showcasing outreach and teaching tool